Application Firewall Data Exfiltration over FTP
Once an environment has been compromised and the adversary finds some desirable data the data needs to be removed from the network. In this use case we will assume that FTP is being permitted egress by the firewall.
Step 1 - Deploy the FTP Server
The instructions to build a preconfigured FTP server with TLS encryption can be found here, https://freshdemo.github.io/infrastructure/2020/03/15/infrastructure-ftpovertls.html
This server is configured to provide FTP over TLS using self signed certificates.
Step 2 - Decrypt TLS
Make sure that the NGFW (or other DUT) is decrypting TLS traffic between the source and FTP server. Otherwise you will only see the network connectivity and lose visibility into the files and threats being transferred.
Step 3 - Upload a File
From a blue host behind the firewall login to the FTP server. This server is running FTP over TLS so you should receive a certificate warning that you need to accept. Pay close attention to approve the root certifcate that is from the NGFW.
Default settings in popular clients like Filezilla seem to work ok. The server is setup for passive transfer. You may want to force the client to "require explicit FTP over TLS"
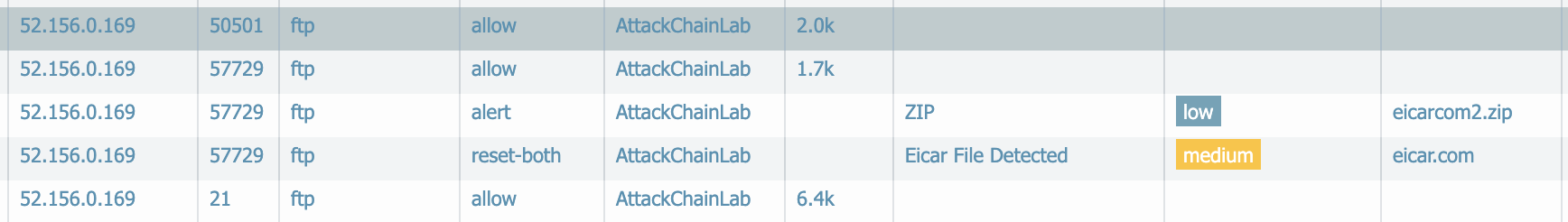
Step 4 - View the Results
Providing TLS decryption and the associated security policies were implemented in a way to permit the traffic you will see something like the following.
The first screenshot indicates that the FTP traffic over port 21 was permitted. From there the data transfer was moved over to TCP port 57729. There are 3 log types; Traffic (firewall), data, and vulnerability.

The second screenshot is showing the same logs just scrolled over to the right to show the additional data available. The data and vulnerability logs show the filename.
For further control you could use the data filtering to block uploads to unknown FTP servers to prevent data loss. The vulnerability profile could be configured to block threats rather than alert.