DNS Subdomain Data Exfiltration
Once an environment has been compromised and the adversary finds some desirable data the data needs to be removed from the network. In this use case we will assume that common protocols like FTP and SSH are heavily restricted on egress traffic (as they should be). One way to move the data is to encode it, making it harder to identify, then split it up into chunks, and apply those chunks as subdomains. So when we even resolve these subdomains they go to the adversary who can stitch them back together and decode them.i
Step 1 - Check out the data
We have some sample data in https://github.com/freshdemo/dnstunnel-subdomains/blob/master/dns_data.txt.
It's base64 encoded so use your favorite decoder to see what the secrets are.
Step 2 - Run the "Script"
With the data already encoded, we have also chopped it up into subdomains, and created a script to resolve them all.
The powershell version for Windows can be found https://github.com/freshdemo/dnstunnel-subdomains/blob/master/dns_tunneling.ps1
The Mac/Linux version can be found https://github.com/freshdemo/dnstunnel-subdomains/blob/master/dns-tunnel.sh
Step 3 - View the Results
The client may not provide a lot of output because all it has to do is try to resolve the domains.
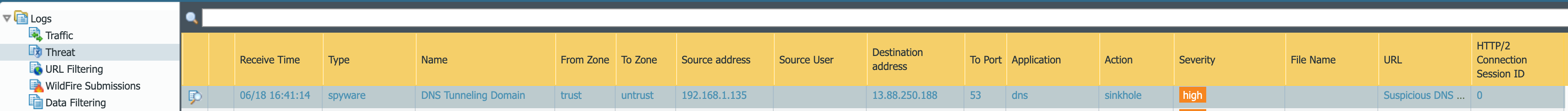
Looking at the following NGFW log we can see that the NGFW prevented the session. It determined that the traffic is attempting to tunnel data in DNS and sinkholed the session. Sinkholing means that the DNS resolution response was modified in transit so that the client doesn't even receive the malicious IP address.