Web Server Compromise - Apache Struts
Remotely exploiting servers in DMZ's seems so unecessary today with all of the credential theft and client side exploitation, but it is still a critical link in the attack chain. Cloud initiatives are allowing administrators to start up servers all over the place, and most of the time they do not have the same protections in the cloud they typically would in the DMZ. This attack could also be applied for lateral movement if the vulnerable web application is only accessible internally.
Step 1 - Deploy the Apache Struts
The intrstructions to build your own vulnerable container can be found here, https://github.com/freshdemo/ApacheStruts-CVE-2018-11776.
Typically I will not re-engineer the whole environment to setup a DMZ for this, but you could. You can also put the container outside the device under testing and the attack will be from the perspective of your internal client exploiting a server outside of the network.
Step 2 - Run the Exploit
From a terminal behind your device under testing, run the exploit against the vulnerable server.
python ./exploit.py http://13.88.250.188:8080 'id'
Your output should look like this, providing nothing was in the way preventing the attack.
root@k:/home/s# python ./exploit.py http://13.88.250.188:8080 'id' [*] CVE: 2017-5638 - Apache Struts2 S2-045 http://13.88.250.188:8080 : [*] cmd: id uid=0(root) gid=0(root) groups=0(root)
Step 3 - View the Results
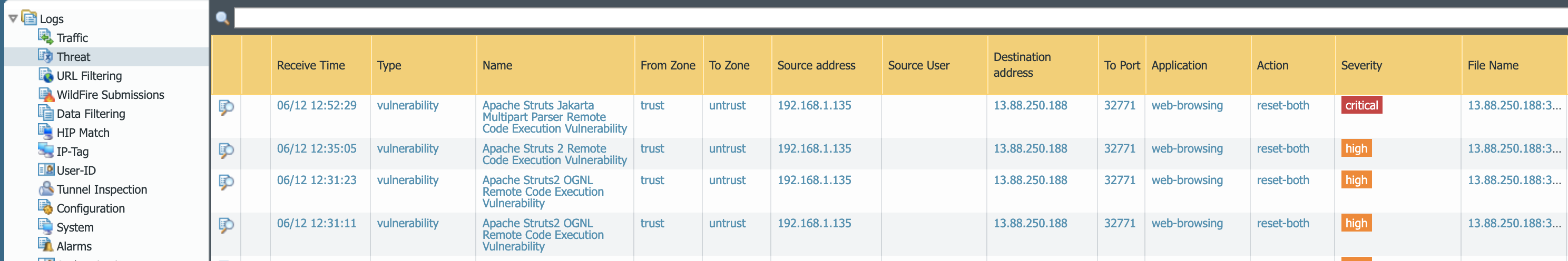
Looking at the following NGFW log we can see that the NGFW prevented the session.
You will notice that there are actually 3 alerts that have triggered; Apache Struts2 OGNL Remote Code Execution Vulnerability, Apache Struts 2 Remote Code Execution, and Apache Struts Jakarta Multipart Parser Remote Code Execution Vulnerability. The reason there are 3 is because after the first the detection an exception was made for the first alert and the attack was run again, and subsequently prevented by the second alert. The second alert was then added to the exceptions and the exploit was run again resulting in the third alert.