Spearphishing Link
One of the first steps during an incident or breach is phishing, where a user will be lured to a website that will either convince users to input their credentials, have them execute malware, or take advantage of a vulnerability to run further commands to gain a better foothold.
Step 1 - Deploy the Phishy Infrastructure
Using the following Docker container will allow you to run SMTP, IMAP, and DNS to facilitate these attacks, https://github.com/freshdemo/mailanddns. See the README on how to deploy and run the container.
Step 2 - Deploy Kali/Social Engineering Toolkit
Deploy this in the same environment as the Phishy Infrastrucutre. Azure has a Kali image you can add directly to your Resource Group.
Once your red host is running deploy and configure a local MTA that will send emails through your phishy mailserver, https://github.com/freshdemo/smarthost. The steps to set this up and in the README.
Step 3 - Setup an Email Client
Below you will find the what Thunderbird and Mail look like configured.
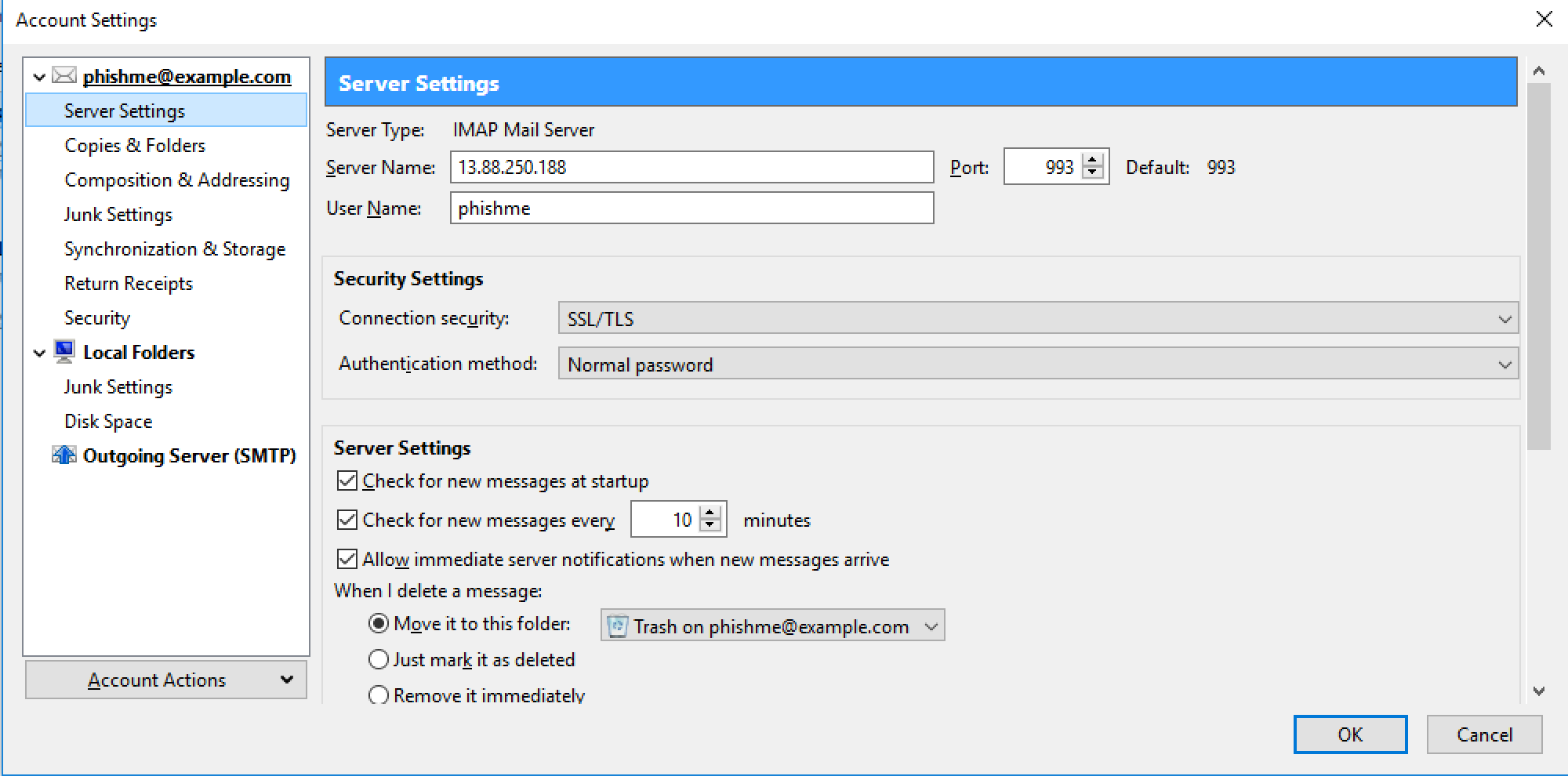 Thunderbird Configured
Thunderbird Configured
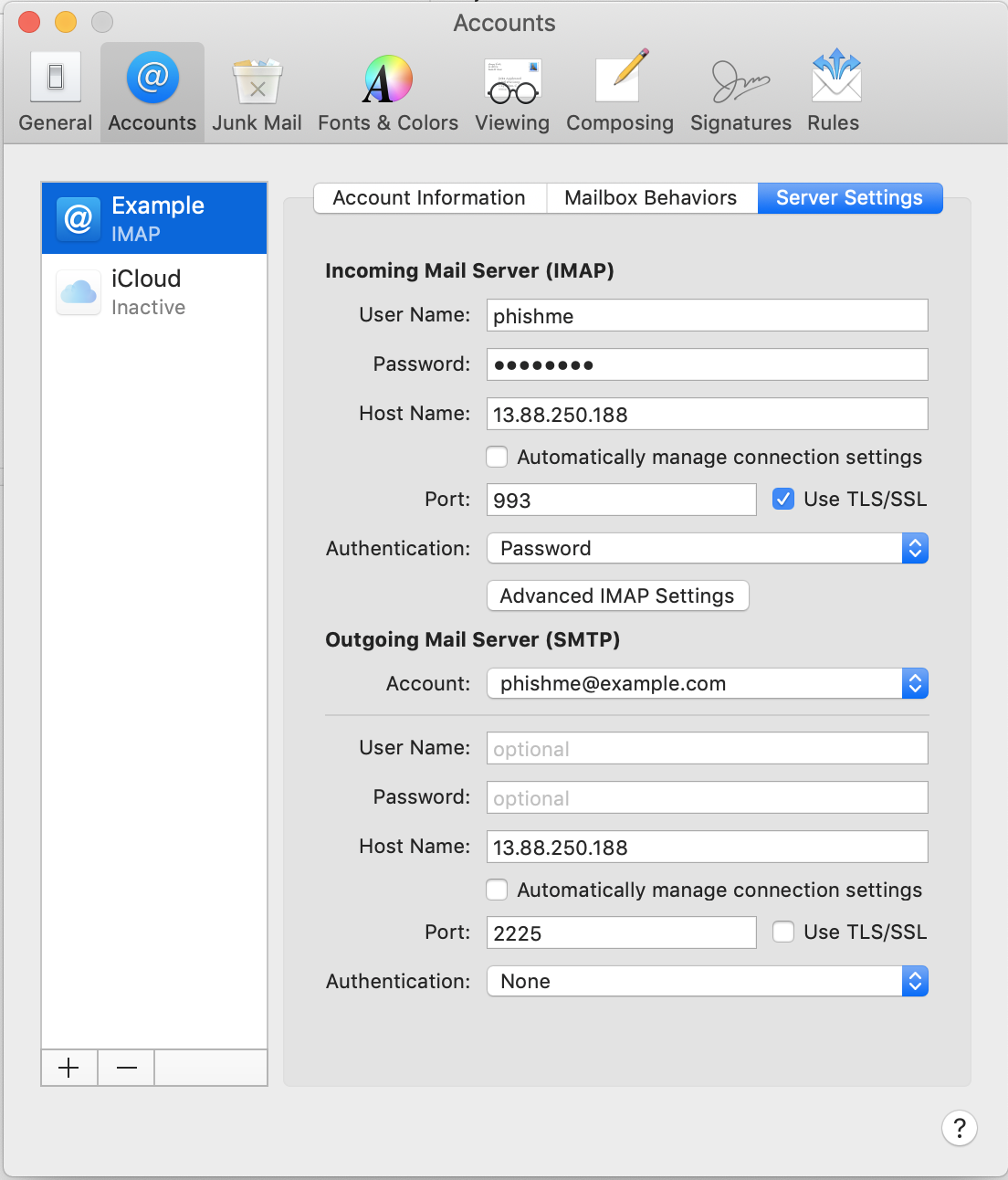 Mail Configured
Mail Configured
Step 4 - Send a Malicious Email
You can either use the Social Engineering Toolkit, or for a quicker way you can also find the test file fullmail.txt in the freshdemo/smarthost repo. It is already configured to send an email to the phishme account. Feel free to edit the file and send the mail with;
sendmail -t < fullmail.txt
Step 5 - View the Email
You should have the email in the configured client. Be careful of the link as it is live fire at the time of this writing, and is currently being blocked in this environment due to enterprise network security services.
The arrows indicate;
- the link in the body of the email is obfuscated with regular text follow these instructions
- when you mouse over the link, the real address shows up in the status bar at the bottom.
- when the link is clicked (don't do it) the page can't currently be reached.
</ul>
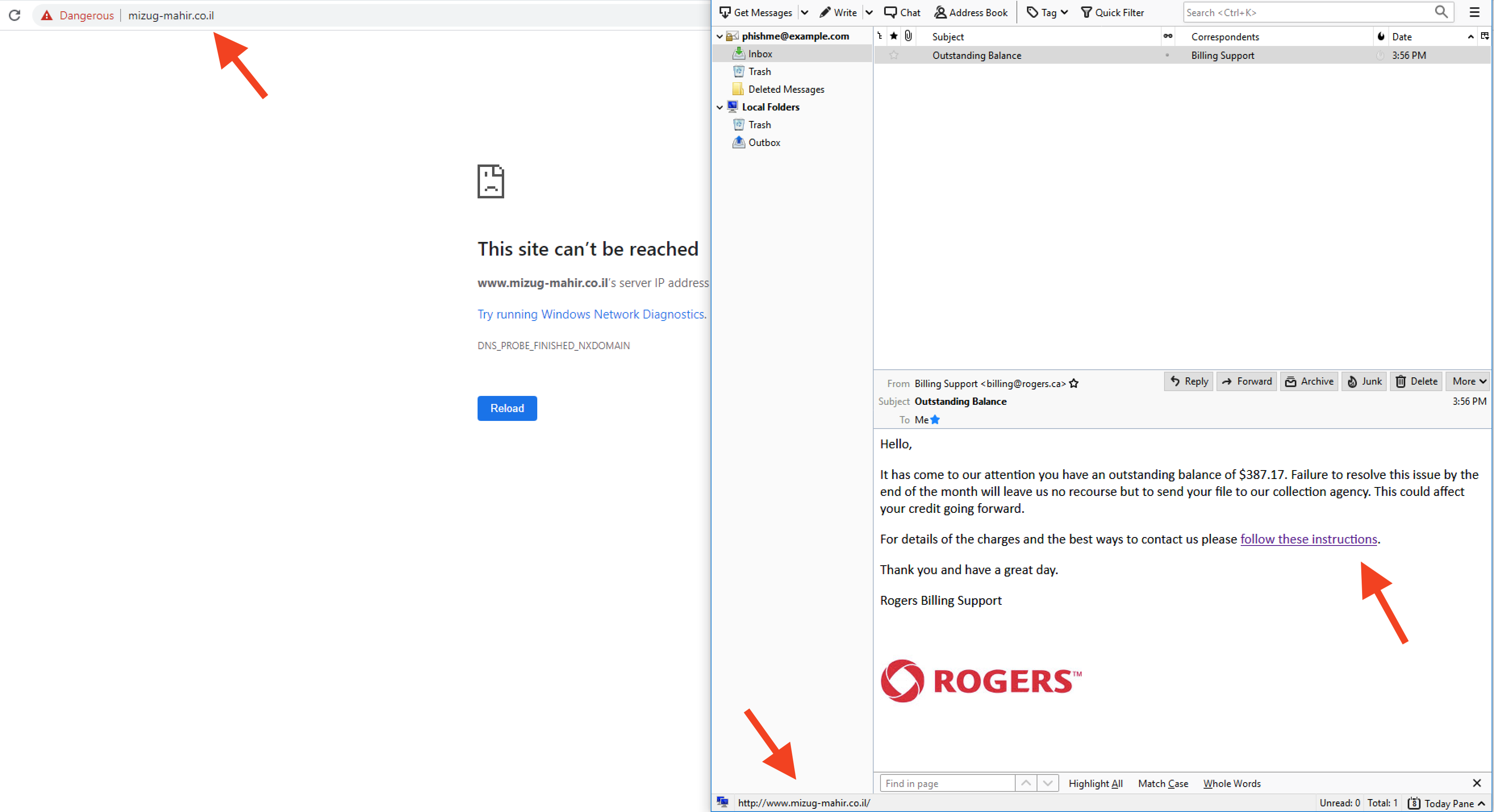 Spearphished Link
Spearphished Link
Step 6 - View the Protection on the NGFW
The log below indicates that the domain clicked from the email was sinkholed. This means that when this target computer was asking what the IP address is of the domain even that traffic was dropped. Because it was sinkholed the real IP of the malicious server will not be known to this client so any attempt to connect by name is prevented.
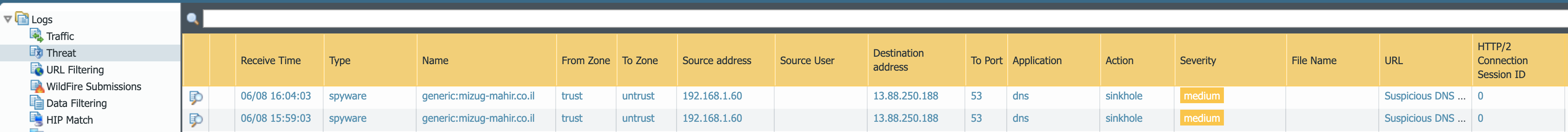 Spearphished Link Sinkhole
Spearphished Link Sinkhole